Project Address: https://github.com/f0ng/captcha-killer-modified#
Recognition Library: https://github.com/sml2h3/ddddocr
0x01 Installation#
Prerequisites: Install dddocr.
pip3 install ddddocr
Use the provided jar file and py file, and modify line 17 of the py file, otherwise an error will occur.
async def handle_cb(request): img_base64=await request.text() return web.Response(text=ocr.classification(img_base64))
0x02 Start#
Start the Python script
Python3 codereg.py

Get Captcha
Intercept the package requesting the captcha, for example:
http://127.0.0.1/yanzheng/yanzhengma.php
And right-click to send it to the captcha panel
![]()
Fill in the captcha URL and click "Get", the captcha image will be displayed on the right.

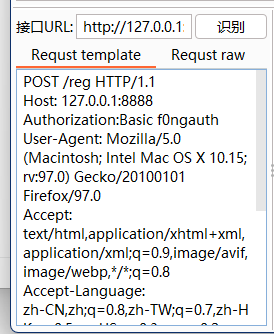
Fill in the interface URL and request template
The template is as follows:
POST /reg HTTP/1.1 Host: 127.0.0.1:8888 Authorization:Basic f0ngauth User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:97.0) Gecko/20100101 Firefox/97.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: keep-alive Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded Content-Length: 8332 <@BASE64><@IMG_RAW></@IMG_RAW></@BASE64>
After filling in, click "Recognize" to recognize the captcha image just obtained.
Click "Recognize" repeatedly to recognize multiple images.
Click "Get" once and click "Recognize" once to recognize images one by one.
Used to observe whether the captcha recognition on the right is accurate.

0x03 Capture Login Package Brute Force#
Turn on the interception switch, intercept and capture the login operation package, and send it to the Intruder module
Select attack mode: Pitchfork
Mark the fields for the password and captcha values

The first payload is the value of the username:

The second payload is the value of the captcha:
The mode has changed, and the plugin needs to be loaded.

PS: Note that you need to set single-threaded mode, otherwise the captcha will be mixed. It is also best to set a delay.

Then, attack.

The specific recognition situation can also be seen on the plugin page.

0x04 Done#
Can only recognize some simple graphics, arithmetic is not supported.
