0X01#
Received a customer notification, found a suspected phishing email, and requested assessment and tracing.
The email is roughly as follows:
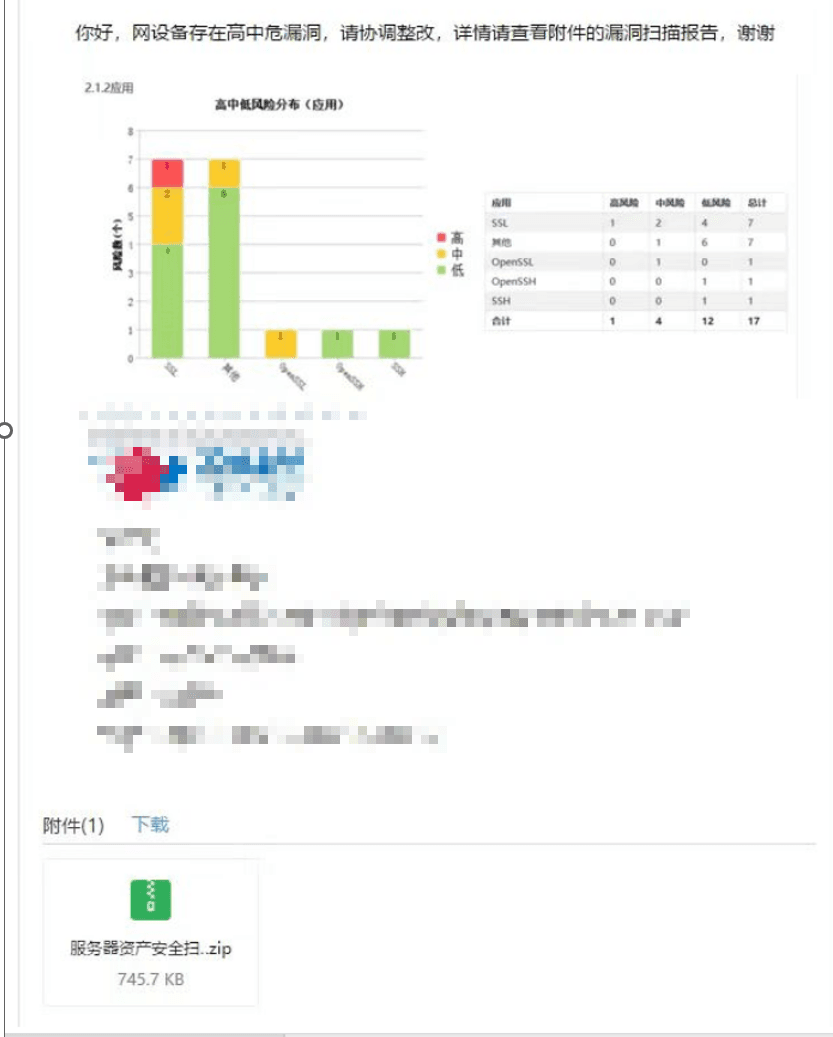
0X02#
After changing the compressed file to EML and opening the file, the contents of the compressed file are as follows:
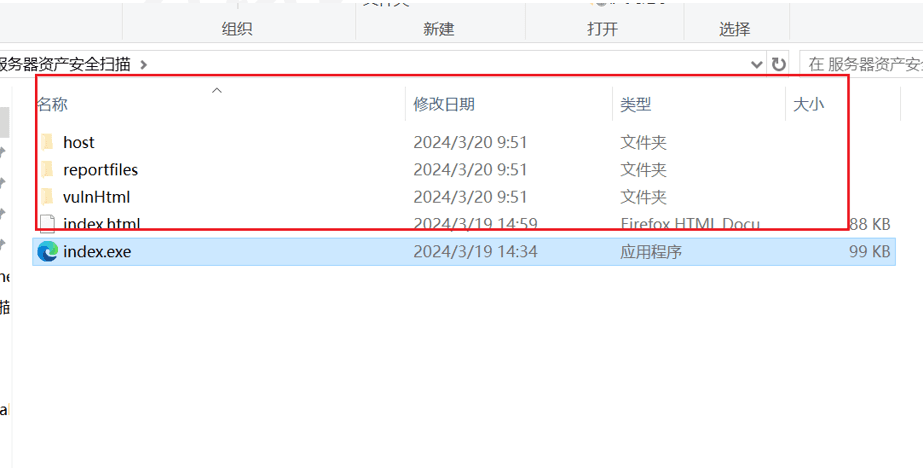
PS: The initial state of the index.exe in this case is index.sc. In order to facilitate analysis, the original suffix has been changed here. The most important executable file is index.exe, which is used to launch the html file through this exe.
At the beginning, I didn't understand the intention. As we all know, the PE header of an executable file under the Windows system is as follows:
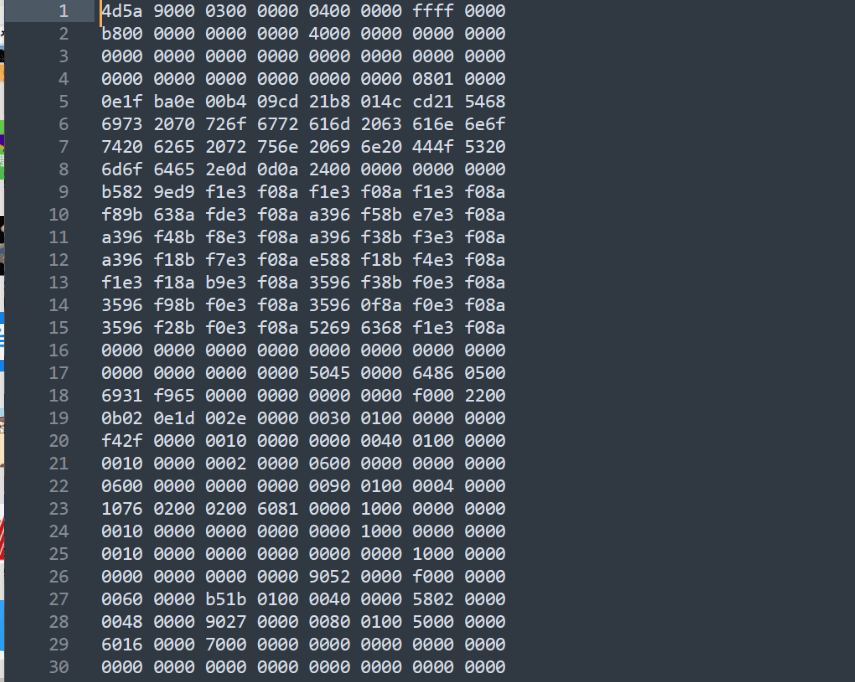
If you open it directly, the status is as follows:
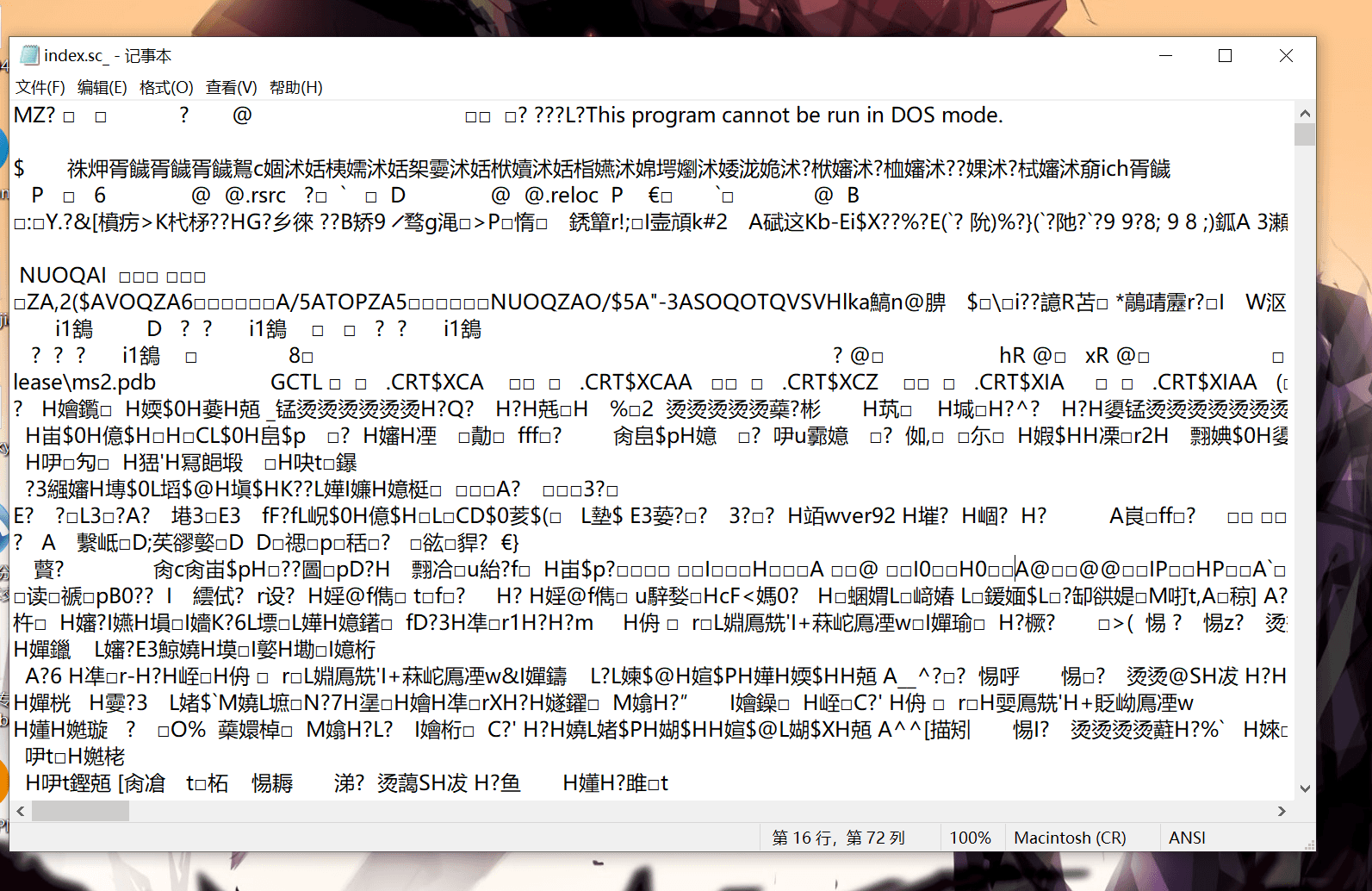
There is something that confuses me here. The .sc file inside is in EXE format, but it will not be executed as an exe by default under Windows GUI. Only console will be executed as EXE.
But for phishing, it definitely needs to be triggered in GUI mode, and here is this kind of writing.
The intention is probably that there is something else to start this file, or it is a mistake...
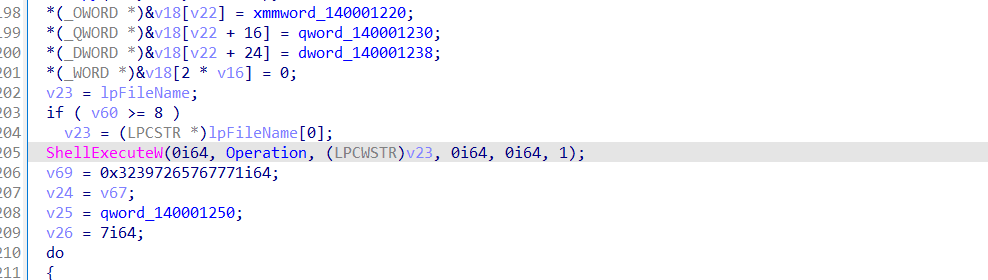
Start the indexrcs.html in the same directory
But the html file in the directory is called index, which does not match the name of the file in the folder.
It seems that the attacker made a mistake.
And both WeiBu and VirusTotal are all green. Here is a picture:
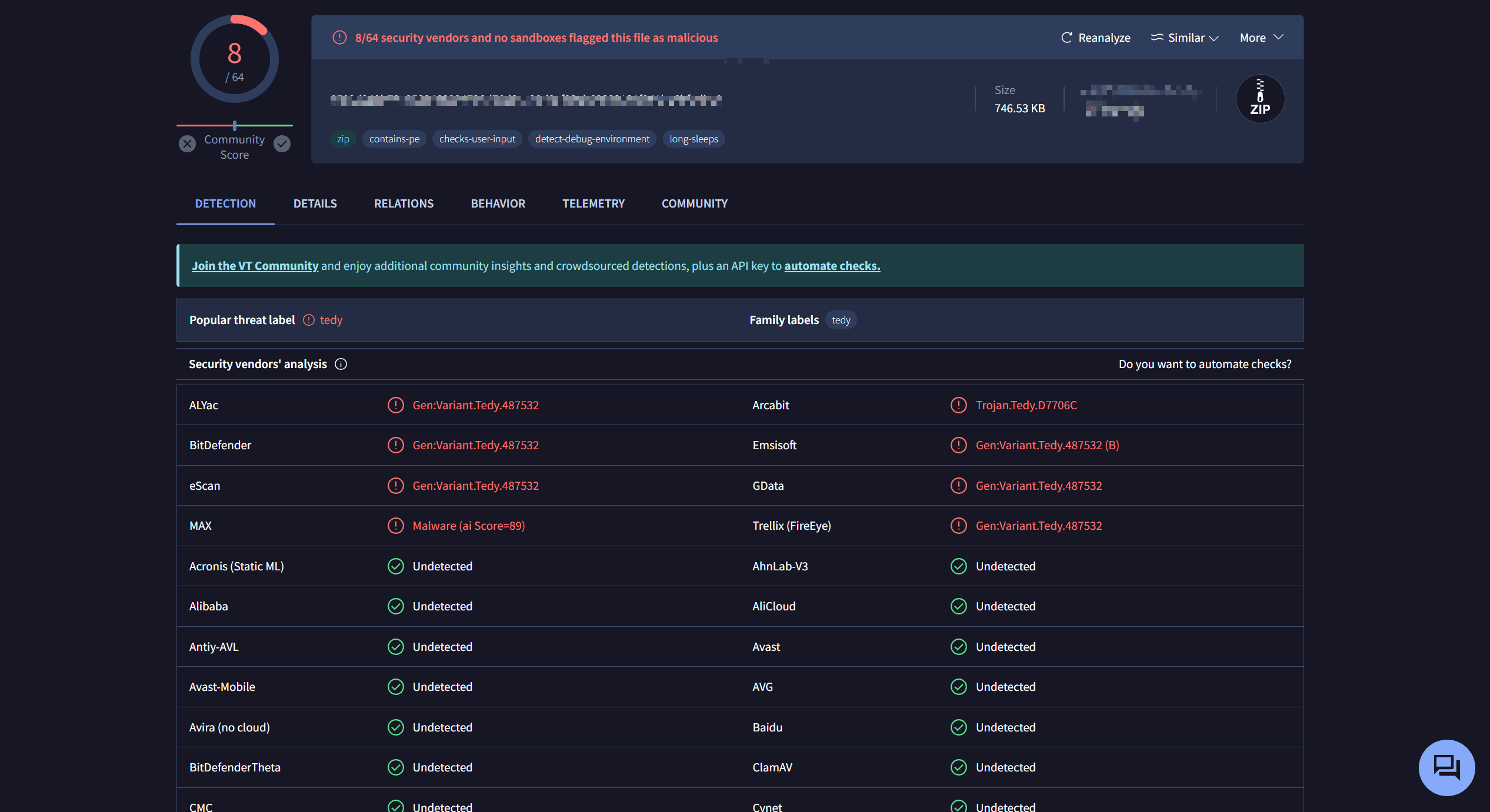
The anti-virtual machine is also well done. It detects the files in your temp directory. If there are fewer files, it will not execute.
There are hundreds of files in the temp directory of a normal physical machine, and the virtual machine is relatively clean.
The overall behavior is to open the index.html file in the same path, which is a normal scan report, and then execute the shellcode, CS Trojan, C2 address: 207.XXX.XXX.XXX.
0X03#
After obtaining the IP, you can try to trace it and collect intelligence on the IP.
Fortunately, I found that a historical resolution is a CN domain name.
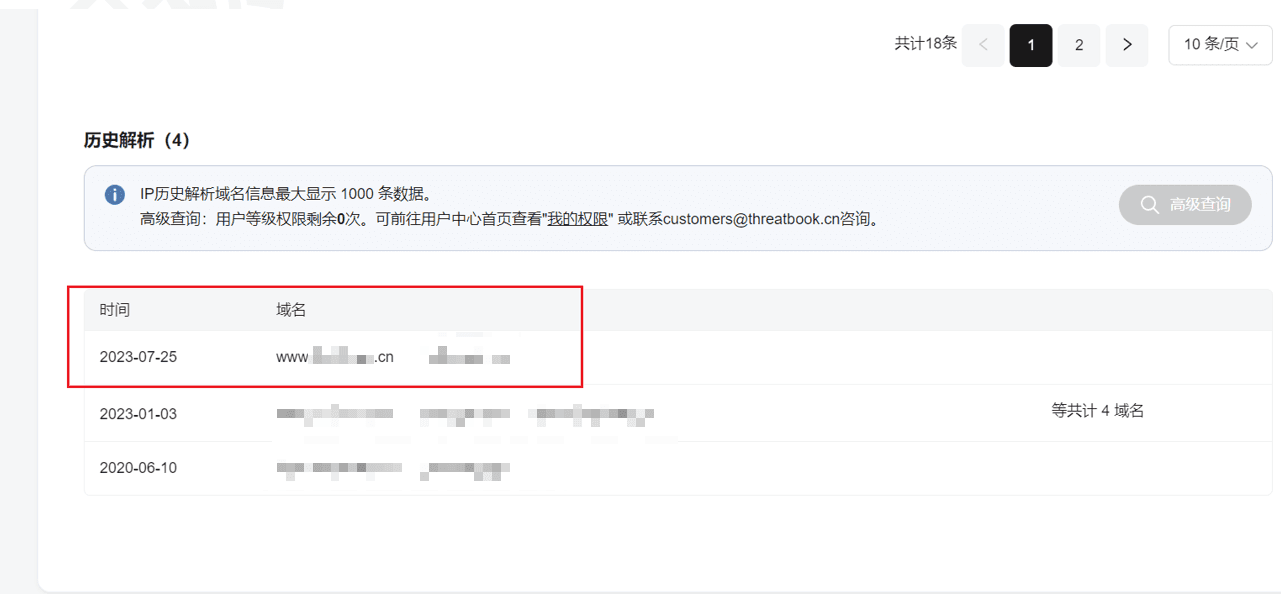
By querying the whois information, the registrant's email information and personal name can be obtained.
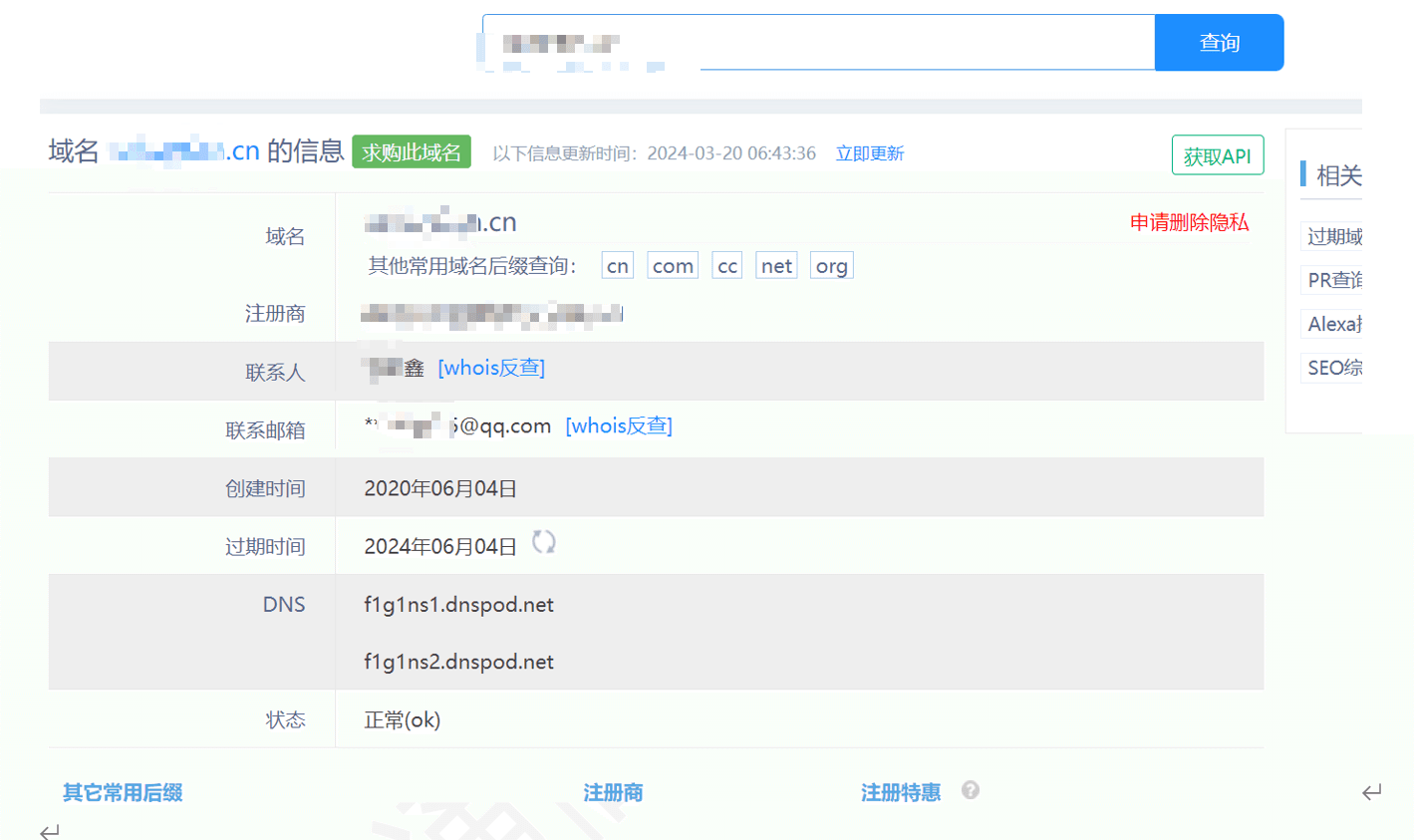
By associating the email with historical information, the following results can be obtained:
Name: xx Xin
Email: ***[email protected]
ID card number: 440********16
Phone number: 176 *** 113
So how to determine if the IP is the real attacker?
As mentioned above, you can query which data center the IP segment belongs to. By querying the IP, it is found that the corresponding service provider is Vultr.
By obtaining the registration account information of Vultr, the result is obtained:
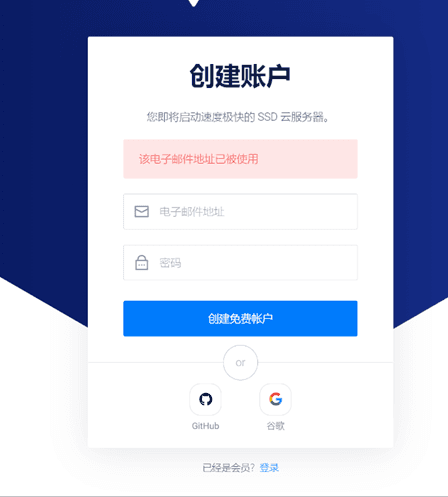
It can be confirmed that the phishing email/malicious IP/domain name/person has all the necessary elements for high-intensity association.
At the same time, intelligence was obtained from a PDF file. It was determined that the employee is a member of the information department of a certain group.

Thanks again to my colleague for providing me with the virus analysis process.
END.